ECCelerate™ 6.3
Core Crypto Toolkits
The following tables list all pre-defined ECC domain parameters. Use the iaik.security.ec.common.ECStandardizedParameterFactory methods to make use of them. You can either provide the curve name (getParametersByName(name) method), use the object identifier (getParametersByOID(oid) method) or select domain parameters by the key length (getParametersByBitLength(bits) method). Some of the curves have more than one name. In this case you can specify any you like.
Supported ECC Domain Parameter for Elliptic Curves over Prime Fields
This is the recommended field type and more efficient in software. The NIST curves are being used if you initialize the keypair generator just with the keysize.
| key length | OID | X9.62 | NIST | SEC2 | RFC 5639 | ANSSI |
| 160 | 1.3.132.0.9 | secp160k1 | ||||
| 160 | 1.3.132.0.8 | P-160 | secp160r1 | |||
| 160 | 1.3.132.0.30 | secp160r2 | ||||
| 160 | 1.3.36.3.3.2.8.1.1.1 | brainpoolP160r1 | ||||
| 160 | 1.3.36.3.3.2.8.1.1.2 | brainpoolP160t1 | ||||
| 192 | 1.2.840.10045.3.1.1 | prime192v1 | P-192 | secp192r1 | ||
| 192 | 1.3.132.0.31 | secp192k1 | ||||
| 192 | 1.2.840.10045.3.1.2 | prime192v2 | ||||
| 192 | 1.2.840.10045.3.1.3 | prime192v3 | ||||
| 192 | 1.3.36.3.3.2.8.1.1.3 | brainpoolP192r1 | ||||
| 192 | 1.3.36.3.3.2.8.1.1.4 | brainpoolP192t1 | ||||
| 224 | 1.3.132.0.33 | P-224 | secp224r1 | |||
| 224 | 1.3.132.0.32 | secp224k1 | ||||
| 224 | 1.3.36.3.3.2.8.1.1.5 | brainpoolP224r1 | ||||
| 224 | 1.3.36.3.3.2.8.1.1.6 | brainpoolP224t1 | ||||
| 256 | 1.2.840.10045.3.1.7 | prime256v1 | P-256 | secp256r1 | ||
| 256 | 1.3.132.0.10 | secp256k1 | ||||
| 256 | 1.3.36.3.3.2.8.1.1.7 | brainpoolP256r1 | ||||
| 256 | 1.3.36.3.3.2.8.1.1.8 | brainpoolP256t1 | ||||
| 256 | 1.2.250.1.223.101.256.1 | FRP256v1 | ||||
| 320 | 1.3.36.3.3.2.8.1.1.9 | brainpoolP320r1 | ||||
| 320 | 1.3.36.3.3.2.8.1.1.10 | brainpoolP320t1 | ||||
| 384 | 1.3.132.0.34 | P-384 | secp384r1 | |||
| 384 | 1.3.36.3.3.2.8.1.1.11 | brainpoolP384r1 | ||||
| 384 | 1.3.36.3.3.2.8.1.1.12 | brainpoolP384t1 | ||||
| 512 | 1.3.36.3.3.2.8.1.1.13 | brainpoolP512r1 | ||||
| 512 | 1.3.36.3.3.2.8.1.1.14 | brainpoolP512t1 | ||||
| 521 | 1.3.132.0.35 | P-521 | secp521r1 | |||
Supported ECC Domain Parameter for Elliptic Curves over Binary Fields
We only support polynomial base representation of this field type.
| key length | OID | X9.62 | NIST | SEC2 |
| 163 | 1.3.132.0.1 | K-163 | sect163k1 | |
| 163 | 1.3.132.0.15 | B-163 | sect163r2 | |
| 163 | 1.3.132.0.2 | sect163r1 | ||
| 191 | 1.2.840.10045.3.0.5 | c2tnb191v1 | ||
| 191 | 1.2.840.10045.3.0.6 | c2tnb191v2 | ||
| 191 | 1.2.840.10045.3.0.7 | c2tnb191v3 | ||
| 193 | 1.3.132.0.24 | sect193r1 | ||
| 193 | 1.3.132.0.25 | sect193r2 | ||
| 233 | 1.3.132.0.26 | K-233 | sect233k1 | |
| 233 | 1.3.132.0.27 | B-233 | sect233r1 | |
| 239 | 1.3.132.0.3 | sect239k1 | ||
| 239 | 1.2.840.10045.3.0.11 | c2tnb239v1 | ||
| 239 | 1.2.840.10045.3.0.12 | c2tnb239v2 | ||
| 239 | 1.2.840.10045.3.0.13 | c2tnb239v3 | ||
| 359 | 1.2.840.10045.3.0.18 | c2tnb359v1 | ||
| 409 | 1.3.132.0.36 | K-409 | sect409k1 | |
| 409 | 1.3.132.0.37 | B-409 | sect409r1 | |
| 431 | 1.2.840.10045.3.0.20 | c2tnb431r1 | ||
| 571 | 1.3.132.0.38 | K-571 | sect571k1 | |
| 571 | 1.3.132.0.39 | B-571 | sect571r1 | |
Supported twisted Edward curve domain parameters
ECCElerate supports twisted Edward curves via
iaik.security.ec.ec.EdStandardizedParameterFactory. You can either provide the curve name (
getParametersByName(name) method) or the object identifier (
getParametersByOID(oid) method). The instances named starting with
Curve are for use in the context of X25519 and X448. The instances named starting with
Edwards are for use in the context of EdDSA.
| Name | OID |
| Curve25519 | 1.3.101.110 |
| Curve448 | 1.3.101.111 |
| Edwards25519 | 1.3.101.112 |
| Edwards448 | 1.3.101.113 |
NIST SP-800-57a Part1 Document
| Bits of Security | Example Algorithm | Prime Field ||p|| * | Binary Field m |
| 112 | Triple-DES | 224 | 233 |
| 128 | AES-128 | 256 | 283 |
| 192 | AES-192 | 384 | 409 |
| 256 | AES-256 | 521 | 571 |
*) by ||p|| is meant the length of the binary expansion of the integer p.
The ECCelerate™ Add-On holds algorithms that are (assumed to be) subject to patent claims. In case you want to employ our arithmetical optimizations to gain full performance, you must include iaik_eccelerate_addon.jar into your classpath.
There have been many patents granted and applied for in the field of ECC. This means that this implementation may contain an implementation of an algorithm that is IPR-protected in some country. At this time we are not aware of a specific case, some arithmetical speedups (included in the separate iaik_eccelerate_addon.jar file). If anybody identifies a case of potential patent infringement, we would be grateful if you could inform us about this to enable us dealing with the issue.
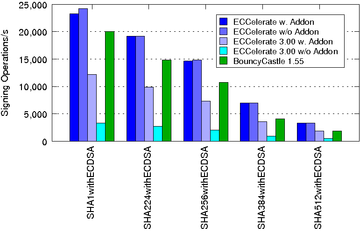
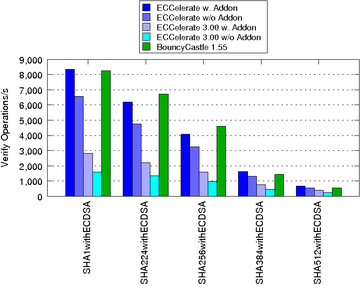
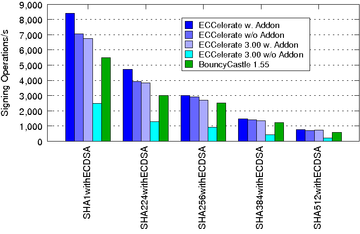
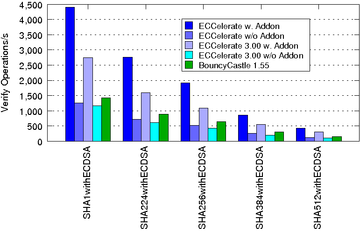
The subsequent charts show the performance improvements of ECCelerate™ with regard to our old IAIK-ECC library. In case of ECCelerate™ the default optimization level was used.
The performance was measured on an Intel(R) Core(TM) i7-4790 CPU @ 3.60GHz, 16GB DDR3 RAM running Ubuntu Linux 15.04/amd64 and JDK 1.7.0_80/amd64 in server mode.
| ECDSA Signing Operations/s using NIST Curves over Fp:
|
| ECDSA Verify Operations/s using NIST Curves over Fp:
|
| ECDSA Signing Operations/s using NIST Curves over F2m:
|
| ECDSA Verify Operations/s using NIST Curves over F2m:
|
For an introduction to the IAIK ECCelerate™ library please have a look at the following Tutorial
The JavaDoc™ API is also available online.
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | B | Fixed addon dependency issue. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | NF | Jar file signed with new JCE code signing certificate. |
| iaik.security.ec.ecdh | Added additional Key Validation in ECDH and EdDH Key Agreement |
|
| iaik.security.ec.ecdsa | NF, C | For deterministic ECDSA signatures the signature value is now verified immediately after creation as countermeasure against fault attacks. The check can be generally en/disabled for all (deterministic and non deterministic) ECDSA signatures by using the static method |
| iaik.cms.ecc.ECCelerateProvider | C | Moved to IAIK-CMS library, thus |
| iaik.cms.ecc.ECCelerateProvider | NF, C | Aligned with IAIK-CMS 6.0 to support S/MIMEv4. |
| iaik.cms.ecc.ECCelerateProvider | C | Fixed AES, DESEde key wrap AlgorithmID parameter field encoding. (aligned with RFC 3278 successor RFC 5753) |
| iaik.cms.ecc.ECCelerateProvider | NF | Support added for key agreement schemes dhSinglePass-stdDH-sha224kdf-scheme, dhSinglePass-stdDH-sha512kdf-scheme, dhSinglePass-cofactorDH-sha224kdf-scheme, dhSinglePass-cofactorDH-sha256kdf-scheme, dhSinglePass-cofactorDH-sha384kdf-scheme, dhSinglePass-cofactorDH-sha512kdf-scheme added. |
| iaik.security.ssl.ECCelerateProvider | C | Also accepts Edwards curve key names starting with “X”. |
| iaik.security.ssl.ECCelerateProvider | C | Support for Ed keys added to |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.common.EdPrivateKey, iaik.security.ec.common.EdPublicKey, | C | Tries to get algorithm name got from algorithm identifier. |
| iaik.security.ec.common.HKDF | NF | HMAC-based Extract-and-Expand Key Derivation Function (HKDF) according RFC 5869. |
| iaik.security.ec.ecdh | NF | ECDH, EdDH KeyAgreement support for HKDF key derivation function. |
| iaik.security.ssl.ECCelerateProvider | C | Also accepts Edwards curve key names starting with “X”. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.common.ECParameters | C | Method |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.common.* | C | Switch for ECPoint so that all functions work in-place if set to true |
| iaik.security.curve.ECPoint | NF | ExtensionFieldElement added exponentiateOutOfPlace function |
| iaik.security.ec.math.field.* | B | Restored backwards compatibility |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.common.* | C | Rework curve parameter storage for better maintainability. |
| iaik.security.curve.ECPoint | B | Ensure that multiplyPoint always works in-place as documented. |
| iaik.security.ec.math.field.* | B | Ensure that exponentiate always works in-place as documented. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.provider.ECCelerate | C | Set default point encoding to uncompressed. Some standards and RFC (e.g. RFC5480) require only support for uncompressed points. Changing the default back to uncompressed points increases the interoperability with libraries not supporting optional point compression. Point compressesions can be enabled using |
| iaik.security.ec.eddsa.* | B | Correctly handle ByteBuffers without underlying arrays. |
| iaik.security.ec.math.curve.* | B | Fix multi-threaded evaluation of pairings involving shared instances of points. |
| iaik.security.ec.* | B | Fix instantiation of the ECCelerate provider and Pairing instances in a multi-threaded environment. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.eddsa | NF | Add support for EdDSA using curves Ed25519 and Ed448 (RFC8032). Since some proposed RFCs are not finalized at the time of the release, we consider the current implementation as experimental. Please note that OneAsymmetricKey-encoded private keys containing the corresponding public key are only supported if IAIK JCE 5.52 or newer is used. Some interfaces might change in the future, so we recommend to follow the examples in the tutorial to be unaffected by future changes in the interface. |
| iaik.security.ec.ecdh | NF | Add support for X25519 and X448. We note that comments regarding EdDSA support also apply here. |
| iaik.security.ec.ecdsa | NF | Add support for deterministic signing (RFC6979). |
| iaik.security.ec.math.curve.Pairing | NF | Add method to evaluate pairing products more efficiently. |
| * | B | Fix Specification-Version of JAR files. |
| iaik.security.ec.math.curve.BarretoNaehrigSWHasher | B | Fix hashToPoint() producing points outside the group for some Barreto-Naehrig curves. |
| iaik.security.ec.math.curve.Comb*ScalarMultiplier | B | Fix incorrect points returned for large scalars when using the Comb scalar multipliers. |
| * | C | Since EdDSA and X25519/X448 require features from newer IAIK JCE versions, ECCelerate now depends on IAIK JCE 5.51 or later. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | C | JAR files are now signed with old (for supporting old DSA JCE Root CA) and new (for supporting new RSA JCE Root CA) IAIK-JCE provider certificates. The new certificate provides a stronger protection (SHA256withRSA) than the old one (SHA1withDSA). The new JCE Root CA is effective for Java versions 8u121, 7u131, 6u141 upwards. To support other (former) Java versions the JAR files must be signed with the old provider certificate, too. |
| iaik.security.ec.ecdsa.* | B | Fix regression when verifying multiple signatures in parallel. |
| iaik.security.ec.math.field.* | B | Fix regression when exponentiating with an int larger than 63. |
| iaik.security.ec.math.field.BinaryField | B | Fix encoding of pentanonimals when explicitly encoding curve parameters. |
| iaik.security.ec.common.EllipticCurve | B | Fix cofactor check to use the correct security level. |
| iaik.security.ec.math.* | NF | Improve loading of addon algorithms and data. |
| * | NF | Improve test coverage of serialization and deserialization functions. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.math.curve.* | NF | Add support for curves from FIDO ECDAA Draft 02 February 2017. |
| iaik.security.ec.math.curve.* | C | Throw an exception on unknown named Barreto-Naehrig curves. |
| iaik.security.ec.math.curve.WNAFMultiplier | B | Performance improvements in binary curve implementations. |
| iaik.security.ec.math.curve.Coordinate | B | Set visibility back to public. |
| iaik.security.ec.math.curve.* | B | Fix instantiation of curves and extension fields in Barreto-Naehrig curve factories. As a side-effect, this change reduces memory consumption when using pairings. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.ecdsa.* | NF | Added support for SHA-3 variants of ECDSA (requires IAIK JCE version 5.3 or later). |
| iaik.security.ec.math.* | NF | Tremendous performance improvements in prime field implementations. |
| iaik.security.ec.math.* | NF | Tremendous performance improvements due to switch to fixed size multi-precision integer implementation. |
| iaik.security.ec.math.* | NF | Performance improvements in binary curve implementations. |
| iaik.security.ec.math.curve.* | NF | Improvements in scalar multipliers. |
| iaik.security.ec.math.curve.* | NF | Added support for ISO_P512, DSD_P256, TPM_ECC_BN_P256 and TPM_ECC_BN_P512 curves. |
| * | NF | Added support for basic side-channel protection. |
| iaik.security.ec.math.curve.* | NF | Added speed-ups for SECP-exclusive (i.e., secp*k1) prime curves to addon. |
| * | NF | Added more curve parameters (for legacy support from older standards). |
| * | C | Now requires Java 6 or newer. |
| iaik.security.ec.math.curve.* | C | Moved some speed-ups (that is, fixed-base comb multipliers) to the base package since the patent expired. |
| * | B | Bug fixes in ECMQV, ECIES and ECDH. |
| * | B | Minor bug fixes. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.curve. AtePairingOverBarretoNaehrigCurveFactory | NF | Allow one to specify more custom parameters. |
| iaik.security.ec.ecies.ECIES | NF | Provide implementation of engineGetKeySize. |
| iaik.cms.ecc.ECCelerateProvider | B | Fix shared key generation for ecka_eg_X963KDF_SHA384/512. |
| iaik.security.ec.math.field.PrimeField | B | Fix computation of buffer lengths. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.common.ECStandardizedParameterFactory | B | Fixed possible NullPointerException with JDK8 |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | NF | Added support for asymmetric pairings over Barreto-Naehrig curves:
|
| * | C | Up to ~24% performance improvements for NIST prime curves |
| * | C | Up to ~15% performance improvements for binary curves |
| * | C | Drastically reduced overall memory consumption |
| * | C | Set default point encoding to COMPRESSED |
| * | B | Fixed compatiblity issues with JDK8 (which requests curves via OIDs) |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.ecdh.ECDHKeyAgreement, iaik.security.ec.ecdh.ECDHWithCofactorKeyAgreement, iaik.security.ec.ecmqv.ECMQVKeyAgreement | NF | engineGenerateSecret: recognizes algorithm “TLSPremasterSecret” as used by JSSE 1.6 |
| iaik.security.ec.common.EllipticCurve | NF | Added more methods for curve arithmetic in wrapper class |
| iaik.security.ec.common.ECPrivateKey | B | Fixed problem with RFC 5915 compliance |
| iaik.security.ec.ecdh.ECDHKeyAgreement, iaik.security.ec.ecdh.ECDHWithCofactorKeyAgreement, iaik.security.ec.ecmqv.ECMQVKeyAgreement | B | Fixed length of encoding in last phase |
| * | B | Further bugfixes |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | NF | Point compression now also available in non-addon version! |
| * | C | High overall performance improvements (up to 15%)! |
| * | C | Reduced memory consumption! |
| * | C | Tremendous performance improvements for ECCelerate w/o addon: Up to 3.7x in case of NIST binary curves and up to 3.2x in case of NIST prime curves! |
| * | C | Tremendous performance improvements for secp160k1, secp160r1, secp160r2, secp192k1, secp224k1 and secp256k1 curves! |
| * | C | Performance improvements for the Brainpool curves! |
| * | B | Several bugfixes related to binary Koblitz curves and non-default optimization levels (Addon) |
| iaik.security.ec.ecies | B | Fixed bug in ECIES implementation related to HMAC/SHA, XOR modes |
| * | B | Javadoc corrections |
| iaik.security.cms.ECCelerateProvider | NF | Support for BSI TR-03109 |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.cms.ecc | C | ECCelerateProvider no longer final. |
| iaik.security.ssl | C | ECCelerateProvider no longer final. |
| iaik.security.ec.math.field | B | Fixed rarely occurring bug in arithmetical subroutine. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | C | Slight performance improvements. |
| * | C | Reduced memory consumption in some situations. |
| * | B | Minor bugfixes. |
| * | B | Some Javadoc corrections. |
| iaik.security.ec.math.curve | NF | Support for multiple simultaneous scalar multiplications. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | C | FIPS 186-4 compliance. |
| * | NF, C | jar files signed with new JCE code signing certificate. |
| * | NF | additional signed jar files with the Trusted-Library attribute. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | NF | Added curve FRP256v1. |
| * | C | Lots of (minor) performance improvements. |
| * | B | Some small bugfixes. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | NF | ECMQV protocol implemented (addon only). |
| * | NF | ECIES protocol implemented. |
| * | NF | Fast Koblitz curve implementations (addon only). |
| * | NF | (Re)included P-160, secp160k1, secp160r2 curves. |
| * | C | Tremendous performance improvements for secp*k1 curves. |
| * | C | Check for SP800-57 recommended parameters no longer turned on by default. Furthermore, the FIPS-186 PRNGs are now being used by default for key generation. |
| * | C | Tremendously improved performance of some prime field implementations (Brainpool and P-256, P-512 if addon not enabled) |
| * | C | Lots of minor performance improvements, slightly reduced memory footprint and some minor bugfixes. |
| iaik.security.ec.math.curve.ECPoint | B | In some cases equals() returned incorrect results. |
| iaik.security.ec.ecdh | C | Moved types KDFParameterSpec, KeyDerivationFunction, X963ASN1SharedInfo, X963KDFParameterSpec, and X963KeyDerivationFunction to package iaik.security.ec.common |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | C | Optimization levels now affect the whole library, not only addon-related algorithms. |
| * | B | Minor bugfixes and javadoc corrections. |
| * | C | Tremendous performance improvements for prime SECG curves (up to 79%). |
| iaik.security.ec.ecdsa | C | Up to 10% better performance for prime curve ECDSA (regardless of addon). |
| iaik.security.ec.ecdsa | C | Non-addon version: up to 88% better performance for prime curve ECDSA. |
| iaik.security.ec.ecdsa | C | Non-addon version: removed concurrent ECDSA signature verifications, due to performance penalties because of synchronization. |
| iaik.security.ec.common.ECKeyPairGenerator | B | Fixed detection of invalid inputs to newElement(). |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.security.ec.math.field.PrimeField | B | Fixed detection of invalid inputs to newElement(). |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | NF | Introduced performance profiles that allow the user to set the memory/computation time tradeoff for ECDSA signature generations using the addon |
| * | C | Using the default performance profile, ECDSA signature generation is 50% faster compared to version v1.03 |
| * | C | Performance improvements of scalar multipliers using precomputations shipped with the addon |
| * | C | Small performance improvements of WNAF scalar multiplier |
| iaik.security.ec.ecdsa.* | C | Small performance improvements of ECDSA verifications |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | C | Improved overall performance by 5-10% |
| * | C | Added trademark |
| iaik.security.ec.math.field | B | Removed carry-propagation bug in multiprecision integer addition routine |
| iaik.security.ec.math.curve | C | Corrected misspelling: renamed EllipticCurve.constainsPoint() to EllipticCurve.containsPoint() |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | B | Fixed severe performance problems, which only occur in 32-bit Windows JVM, due to bad clone() performance |
| * | B | Fixed problems with obfuscator that led to truncated throws declarations |
| * | B | Fixed potential NullPointerException() thrown in some equals() implementations |
| demo.ECCelerateAddonDemo | NF | Added demo to illustrate addon registration process |
| iaik.security.ec.common.EllipticCurve | C | ECStandardizedParameterFactory now sets the curve’s generator in method getParamSpec() |
| iaik.security.ec.ecdsa.* | C | On verify the security strength of involved algorithms and parameters is no longer checked |
| iaik.security.ec.provider.ECCelerate | NF | Added new methods: enforceSP80057Recommendations() and areSP80057RecommendationsEnforced(). enforceSP80057Recommendations() allows the user to disable the security strength checks recommended by NIST SP800-57 for algorithms and parameters used in combination with ECDSA. Note that these checks are enabled by default |
| iaik.security.ec.common.EllipticCurve | B | Fixed byte[] to BigInteger conversion problem in decode() |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | B | Improved overall code robustness |
| iaik.ec.math.field.BinaryField | C | Type of CHARACTERISTIC_TWO_*_OID members changed from String to ObjectID |
| iaik.ec.math.field.BinaryField | B | Bug removed, where CHARACTERISTIC_TWO_GN_BASIS_OID was passed as String to the encoding routine and not as ObjectID |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| iaik.ec.ecdsa.* | C | Improved ECDSA verify performance |
| iaik.ec.math.field | B | Bugfix in reduction routine of prime Field Fp521 in addon |
| iaik.ec.common.ECKeyFactory | B | ECKeyFactory can now deal with java.security.spec.EC*KeySpec |
| iaik.ec.common.ECParameterSpec | B | ECParameterSpec.getParameterSpec(params) no longer loses the OID, if params is instance of IAIK ECParameterSpec |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | C | Overall performance improvements (up to 20%) due to simplified handling of precomputations. |
| * | B | Added comprehensive parameter checks. |
| * | C | The addon is now loaded automatically, if the file iaik_eccelerate_addon.jar is located in the same directory as iaik_eccelerate.jar. |
| iaik.security.ec.common.ECKeyFactory | C | ECKeyFactory can now deal with all kinds of encoded EC keys. |
| iaik.security.ec.common.ecdh.* | B | Fixed missing precomputations. |
| iaik.security.ec.common.ecdsa.* | B | Fixed missing precomputations. |
| iaik.security.ec.math.ec | C | Renamed package to iaik.security.ec.common.math.curve |
| iaik.security.ec.provider.ECProvider | C | Added more algorithm aliases. |
| iaik.security.ec.common.ECParameterSpec | B | Fixed bug that prevented ECParameterSpec.decode(ASN1Object) from decoding OIDs. |
| iaik.security.ec.common.SecurityStrength | B | Previously, SecurityStrength only recognized SPI-based SecureRandoms. |
| iaik.security.ec.provider.ECProvider | C | Renamed class to ECCelerate. |
| iaik.security.ssl.IAIKECProvider | C | Renamed class to ECCelerateProvider. |
| iaik.cms.ecc.IAIKECProvider | C | Renamed class to ECCelerateProvider. |
| Class or Package | Bug / Change / New Feature | Description and Examples |
|---|---|---|
| * | NF | First release of the new IAIK ECCelerate crypto library |